
What is Secure Coding? Techniques, Standards, and Resources
When software vulnerabilities are treated as an afterthought or roadblock to innovation, organizations open the door to data breaches, reputational damage, and costly legal liabilities. Cyberattacks often exploit weaknesses in code that might have been prevented with stronger development practices.
Secure coding addresses these challenges by embedding security principles into every stage of development. Instead of implementing fixes after vulnerabilities are discovered, developers write code with built-in protections against common threats such as injection attacks and cross-site scripting (XSS). Let’s take a closer look at how secure coding can help your company reduce risk, safeguard user trust, and comply with regulatory requirements, all while delivering reliable, high-quality software.
What is secure coding?
Secure coding is the principle of following security best practices when writing software to address potential vulnerabilities. Rather than treating security as a separate phase of development, secure coding integrates proven safeguards from the earliest stages on, ensuring developers take ownership of code security and have the skills to apply it effectively.
Recognized secure coding standards produced by organizations like the Open Worldwide Application Security Project (OWASP), or the Software Engineering Institute’s CERT Division, can act as a North Star for developers looking to avoid common pitfalls that attackers exploit. Continuously building upon foundational, hands-on secure coding skills to safely implement these strategies into existing workflows is a non-negotiable in today's cybersecurity landscape. For example, validating as many user inputs as possible can prevent SQL injection attacks, while output encoding helps block XSS. These and other secure coding practices reduce the risk of breaches and lead to more resilient applications that can stand up to evolving cyber threats.
Why is secure coding so important?
Secure coding matters because many successful cyberattacks exploit vulnerabilities that could have been prevented during development. By prioritizing secure practices from the start, you reduce the likelihood of introducing flaws that attackers can use to compromise data or disrupt operations. Building security into every stage of the software development life cycle (SDLC) ensures that every feature, update, and integration is designed with protection in mind.
Proactively addressing risks during development is far less expensive than fixing them after deployment, where remediation can require emergency patches, downtime, and incident response resources. It improves compliance with data protection regulations as well, sidestepping potential fines and legal challenges. Secure coding practices also foster consumer trust in your company and make strong security part of your brand reputation.
Common code security vulnerabilities
Secure coding aims to prevent the most frequent and dangerous vulnerabilities that attackers exploit, in addition to emerging threat vectors, like those that come with the use of AI coding tools. Here is an overview of several common vulnerabilities, the damage they can cause, and how secure coding can help mitigate them.
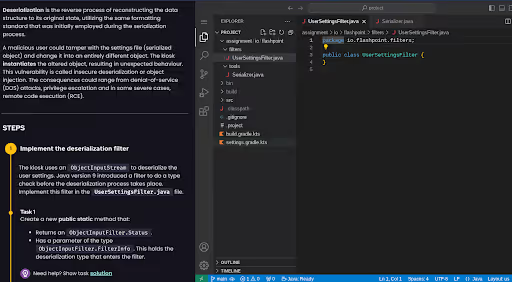
Deserialization flaws
Deserialization flaws occur when an application accepts and processes data from external sources without proper validation. Serialization converts objects into a format that can be stored or transmitted, while deserialization reconstructs those objects for use. The impact of a deserialization flaw can be severe, resulting in the execution of arbitrary code or escalation of privileges. Secure coding addresses this by ensuring that only trusted, validated data is deserialized and by avoiding native deserialization of untrusted inputs entirely when possible.
Injection attacks
Injection attacks occur when an attacker supplies input that is interpreted as part of a command or query by the application. The most well-known type is an SQL injection, where malicious SQL statements are inserted into queries to access or alter database contents. Other types include command injections, where attackers execute arbitrary commands, and Lightweight Directory Access Protocol (LDAP) injections.The consequences of injection attacks are broad, ranging from unauthorized data access and deletion to full system compromise. Databases containing sensitive personal, financial, or proprietary information are prime targets. Secure coding helps prevent injection vulnerabilities by using parameterized queries or prepared statements, escaping untrusted data before it’s processed, and enforcing strict input validation. These and other secure coding practices can stop attackers from altering the intended behavior of the application.
Cross-site scripting (XSS)
Cross-site scripting (XSS) is a form of injection attack that targets web applications by inserting malicious scripts into pages viewed by other users. This typically happens when an application includes unvalidated user input in its output. When another user’s browser renders the page, the malicious script runs, potentially stealing cookies, capturing keystrokes, or redirecting them to malicious sites.
The impact of XSS can include session hijacking and identity theft. For businesses, this erodes customer trust and can lead to regulatory consequences if sensitive data is compromised. Secure coding addresses XSS by sanitizing and encoding all user-supplied input before it’s displayed, using frameworks that automatically escape output, and implementing a Content Security Policy (CSP) to limit what scripts can run.
Access control
Access control vulnerabilities occur when rules about what users can see or do are not properly defined or enforced. Broken access control lets attackers bypass intended user role restrictions, potentially reading sensitive data, modifying records, or performing actions intended only for privileged users.
Access control issues pose a significant challenge, and AI coding tools, in particular, have struggled to address this vulnerability class effectively, highlighting the need for developer skill and awareness. The impact of broken access control is significant. For example, if an attacker can access admin-only features, they could disable security settings, extract private information, or impersonate other users.
Secure coding practices counter these risks by enforcing server-side authorization checks for every request, following the principle of least privilege, and avoiding sole reliance on obscurity (such as hiding links) as a security measure. Additionally, conducting rigorous access control testing helps ensure that these protections remain strong over the long term.
Cross-site request forgery (CSRF)
Cross-site request forgery (CSRF) attacks force a user to perform an unwanted action on another site where they are authenticated. This might be transferring funds, changing an email address, or modifying account settings. The attack works because the browser automatically includes valid authentication tokens, like cookies, with the forged request.
Secure coding defends against CSRF by implementing anti-CSRF tokens that are unique to each user session and validating them with each state-changing request. Additional defenses include requiring re-authentication for critical actions and setting the SameSite attribute on cookies to prevent them from being sent with cross-site requests. By embedding these protections into the development lifecycle, you can make it much more likely that your system processes only legitimate, intentional actions.
Insecure authentication
Insecure authentication occurs when the process of verifying a user’s identity is weak, predictable, or otherwise flawed. This can result from poor password policies, insecure credential storage, or a lack of multi-factor authentication (MFA). Attackers can exploit these weaknesses through a variety of methods, including brute force attacks, credential stuffing, or intercepting unencrypted credentials in transit. The impact of insecure authentication is severe because it can give attackers direct access to user accounts, administrative controls, and sensitive data. Once inside, they can further compromise systems or make off with valuable information.
Secure coding addresses this vulnerability by enforcing strong password requirements, hashing and salting stored credentials, using secure protocols like HTTPS for all authentication exchanges, and integrating MFA to provide an additional layer of verification. Developers should also design login mechanisms to limit failed attempts and detect suspicious activity early, so authentication systems act as a strong line of defense rather than a weak point.
6 secure coding practices to follow
Building secure software involves more than knowing what threats exist. It requires learning and incorporating proven secure coding practices and patterns. The techniques below offer actionable steps developers can take to make security an integral part of every project.
1. Implement user access control
As noted above, user access control means defining and enforcing permissions for each user role in your system. Strong access control prevents unauthorized users from viewing sensitive data, modifying records, or performing administrative actions. It also limits the damage if a user account is compromised, since an attacker will only have the permissions of that account.
Effective user access control requires robust authentication to verify identity, followed by authorization checks to confirm that the authenticated user has permission to perform the requested action. You should regularly review your access control practices to align with the principle of least privilege, giving users the minimum access needed to do their jobs. Access control also relies on regular monitoring to keep policies and users in the system up to date, along with audits that quickly flag any unusual activity.
2. Validate and sanitize data
Validating and sanitizing data involves checking all incoming inputs to ensure they meet expected formats, types, and patterns before processing, then cleaning the data to remove potentially dangerous content. These practices should apply to incoming data from any external source, as even trusted sources can be compromised, so every input should be treated as untrusted until verified. By building validation and sanitization into the development process, you keep your application resilient against common threats like injection attacks.
3. Write in a modern language
Secure coding isn’t just about how you write code. It’s also about choosing tools and environments that make it easier to avoid introducing security flaws in the first place. While moving entirely to a modern language is often not a realistic or efficient option for many enterprises, making at least some use of a modern programming language — and using the latest version of all your chosen languages — can improve software security. Modern languages and frameworks typically offer better memory safety, stronger type checking, and built-in protection against common vulnerabilities. For example, languages like Rust and Go are designed with safety in mind, helping to prevent issues like buffer overflows that older languages may be more prone to.
Established languages like Java or Python can be difficult to modernize and secure, but keeping up with the most recent releases ensures you have access to the latest security features and performance improvements. Many updates patch known vulnerabilities, deprecate unsafe functions, and provide more secure default settings.
4. Practice code obfuscation
Code obfuscation is the process of making your source code or compiled code more difficult for attackers to understand, reverse-engineer, or manipulate. While it doesn’t replace other security measures, it adds another layer of defense by hiding the application’s logic and sensitive routines from prying eyes. Obfuscation can involve techniques like renaming variables and functions to meaningless identifiers or restructuring code in ways that make it harder to follow.
The goal is to raise the cost and effort required for an attacker to find and exploit vulnerabilities. In secure coding, obfuscation works alongside other strong security practices to make your application a less attractive target.

5. Scan and monitor your code
Secure coding practices also involve actively scanning and monitoring your code. Static application security testing (SAST) tools analyze your source code for known vulnerabilities before deployment, while dynamic application security testing (DAST) tools test running applications for exploitable flaws in real time. Combining both approaches helps you catch issues early and continuously.
Beyond scanning during development, it’s critical to implement ongoing monitoring in production. This involves setting up alerts for unusual activity, logging security events, and utilizing runtime application self-protection (RASP) tools to detect and block attacks in real-time. Regular scanning and monitoring ensure that even if vulnerabilities slip through during development, you have the visibility to address them rapidly before significant damage can be done.
6. Document and implement secure coding standards
Documenting secure coding standards consists of creating a clear set of guidelines that define how your team writes safe, maintainable, and compliant code. These standards should cover topics like input validation, error handling, encryption practices, and session management, as well as how to address common vulnerabilities specific to your tech stack.
Having these standards in place ensures that all developers, from junior engineers to senior architects, follow the same security principles. When paired with training and regular updates, these standards become a living resource that keeps your development process aligned with the latest security requirements.
Secure coding standards and frameworks
If you’re looking for help in crafting your own coding standards, the popular guidelines below can help. They cover a range of practices that address common vulnerabilities and can help clarify how to align your coding efforts with industry best practices.
OWASP Secure Coding Practices
OWASP is one of the most widely recognized sources for developers who want to embed security into their code from start to finish. It produces key secure coding resources like the OWASP Developer Guide and the OWASP Top 10. OWASP’s approach is highly actionable, offering checklists and coding tips that developers can apply during development.
Following OWASP guidelines benefits teams by creating a common baseline for secure coding across projects. Because OWASP is regularly updated to reflect new threat vectors and attack techniques, organizations can use it to stay ahead of emerging risks. By building OWASP’s principles into your workflow, you improve code quality, reduce vulnerabilities, and align with widely accepted industry guidelines.

NIST Secure Software Development Framework
The National Institute of Standards and Technology (NIST) publishes comprehensive secure coding guidance alongside broader cybersecurity frameworks. In addition to providing information on high-level secure software development practices, the NIST Secure Software Development Framework (SSDF) provides a common vocabulary that improves communication on key issues among and between teams at your company. It focuses on outcomes rather than specific techniques, so it's best as a complement to other standards like OWASP or the SEI CERT Coding Standards.
SEI CERT Coding Standards
Developed by the CERT Division at the Software Engineering Institute (SEI), the SEI CERT Coding Standards focus on preventing security vulnerabilities in specific programming languages, including C, C++, Java, and Perl. Each language-specific standard features secure coding rules, detailed explanations, and examples of both compliant and noncompliant code. As the CERT coding standards address the nuances and quirks of specific programming languages, they’re highly valuable and actionable for developers working in those environments.
Microsoft Security Development Lifecycle
Microsoft’s Security Development Lifecycle (SDL) is a set of practices designed to make security an integral part of the software development process. It includes recommendations on 10 important topics, including threat modeling, security training for developers, and securing the software supply chain. Microsoft uses this approach itself, so organizations benefit from a tested process that aligns developers, testers, and security teams.
ISO/IEC 27001
ISO/IEC 27001 is best known as a standard for information security management systems (ISMS), but it also has strong implications for secure coding. While it focuses on establishing an organization-wide ISMS, it includes principles on secure coding. These recommendations provide high level guidance organizations can follow when working to implement secure coding practices.
AI Security Rules
AI coding tools are more handy than ever, but they can do more harm than good if using them doesn’t result in safe, accurate code. Secure Code Warrior’s AI Security Rules — the first of their kind — provide guidance on secure coding best practices to use with AI tools like GitHub Copilot, Cline, Cursor, and Windsurf. These rules keep your AI coding assistants on track, putting guardrails in place that minimize the risk of insecure code.
Learn how to create secure code from the start
Secure coding is more than just a technical requirement — it’s a critical business advantage. When your team writes secure code from the start, you prevent costly vulnerabilities, reduce the risk of data breaches, and deliver software your customers can trust. Mastering secure coding practices, however, can be particularly challenging without structured guidance. Developers need real-world practice, up-to-date knowledge of evolving threats, and a way to apply security principles confidently in every line of code.
Secure Code Warrior’s ISO 27001 certified and SOC 2 compliant agile learning platform gives your team exactly that. With training on language-specific security best practices, realistic coding challenges, and content curated for a variety of roles, it turns security from an afterthought into a natural part of the development process. Developers build the skills to identify and fix vulnerabilities early, align with industry standards, and take full ownership of code security throughout the software development lifecycle. It's no surprise that companies that use Secure Code Warrior cut software vulnerabilities by 53%, realize cost savings of up to $14 million, and see 92% of their developers want additional training.
If you want to see how your team can write safer, stronger code from day one, book a Secure Code Warrior demo today.


Learn what secure coding really means and how secure coding practices can reduce both vulnerabilities and security-related costs at your company.
Secure Code Warrior makes secure coding a positive and engaging experience for developers as they increase their skills. We guide each coder along their own preferred learning pathway, so that security-skilled developers become the everyday superheroes of our connected world.

Secure Code Warrior is here for your organization to help you secure code across the entire software development lifecycle and create a culture in which cybersecurity is top of mind. Whether you’re an AppSec Manager, Developer, CISO, or anyone involved in security, we can help your organization reduce risks associated with insecure code.
Book a demoSecure Code Warrior makes secure coding a positive and engaging experience for developers as they increase their skills. We guide each coder along their own preferred learning pathway, so that security-skilled developers become the everyday superheroes of our connected world.
This article was written by Secure Code Warrior's team of industry experts, committed to empowering developers with the knowledge and skills to build secure software from the start. Drawing on deep expertise in secure coding practices, industry trends, and real-world insights.


When software vulnerabilities are treated as an afterthought or roadblock to innovation, organizations open the door to data breaches, reputational damage, and costly legal liabilities. Cyberattacks often exploit weaknesses in code that might have been prevented with stronger development practices.
Secure coding addresses these challenges by embedding security principles into every stage of development. Instead of implementing fixes after vulnerabilities are discovered, developers write code with built-in protections against common threats such as injection attacks and cross-site scripting (XSS). Let’s take a closer look at how secure coding can help your company reduce risk, safeguard user trust, and comply with regulatory requirements, all while delivering reliable, high-quality software.
What is secure coding?
Secure coding is the principle of following security best practices when writing software to address potential vulnerabilities. Rather than treating security as a separate phase of development, secure coding integrates proven safeguards from the earliest stages on, ensuring developers take ownership of code security and have the skills to apply it effectively.
Recognized secure coding standards produced by organizations like the Open Worldwide Application Security Project (OWASP), or the Software Engineering Institute’s CERT Division, can act as a North Star for developers looking to avoid common pitfalls that attackers exploit. Continuously building upon foundational, hands-on secure coding skills to safely implement these strategies into existing workflows is a non-negotiable in today's cybersecurity landscape. For example, validating as many user inputs as possible can prevent SQL injection attacks, while output encoding helps block XSS. These and other secure coding practices reduce the risk of breaches and lead to more resilient applications that can stand up to evolving cyber threats.
Why is secure coding so important?
Secure coding matters because many successful cyberattacks exploit vulnerabilities that could have been prevented during development. By prioritizing secure practices from the start, you reduce the likelihood of introducing flaws that attackers can use to compromise data or disrupt operations. Building security into every stage of the software development life cycle (SDLC) ensures that every feature, update, and integration is designed with protection in mind.
Proactively addressing risks during development is far less expensive than fixing them after deployment, where remediation can require emergency patches, downtime, and incident response resources. It improves compliance with data protection regulations as well, sidestepping potential fines and legal challenges. Secure coding practices also foster consumer trust in your company and make strong security part of your brand reputation.
Common code security vulnerabilities
Secure coding aims to prevent the most frequent and dangerous vulnerabilities that attackers exploit, in addition to emerging threat vectors, like those that come with the use of AI coding tools. Here is an overview of several common vulnerabilities, the damage they can cause, and how secure coding can help mitigate them.

Deserialization flaws
Deserialization flaws occur when an application accepts and processes data from external sources without proper validation. Serialization converts objects into a format that can be stored or transmitted, while deserialization reconstructs those objects for use. The impact of a deserialization flaw can be severe, resulting in the execution of arbitrary code or escalation of privileges. Secure coding addresses this by ensuring that only trusted, validated data is deserialized and by avoiding native deserialization of untrusted inputs entirely when possible.
Injection attacks
Injection attacks occur when an attacker supplies input that is interpreted as part of a command or query by the application. The most well-known type is an SQL injection, where malicious SQL statements are inserted into queries to access or alter database contents. Other types include command injections, where attackers execute arbitrary commands, and Lightweight Directory Access Protocol (LDAP) injections.The consequences of injection attacks are broad, ranging from unauthorized data access and deletion to full system compromise. Databases containing sensitive personal, financial, or proprietary information are prime targets. Secure coding helps prevent injection vulnerabilities by using parameterized queries or prepared statements, escaping untrusted data before it’s processed, and enforcing strict input validation. These and other secure coding practices can stop attackers from altering the intended behavior of the application.

Cross-site scripting (XSS)
Cross-site scripting (XSS) is a form of injection attack that targets web applications by inserting malicious scripts into pages viewed by other users. This typically happens when an application includes unvalidated user input in its output. When another user’s browser renders the page, the malicious script runs, potentially stealing cookies, capturing keystrokes, or redirecting them to malicious sites.
The impact of XSS can include session hijacking and identity theft. For businesses, this erodes customer trust and can lead to regulatory consequences if sensitive data is compromised. Secure coding addresses XSS by sanitizing and encoding all user-supplied input before it’s displayed, using frameworks that automatically escape output, and implementing a Content Security Policy (CSP) to limit what scripts can run.
Access control
Access control vulnerabilities occur when rules about what users can see or do are not properly defined or enforced. Broken access control lets attackers bypass intended user role restrictions, potentially reading sensitive data, modifying records, or performing actions intended only for privileged users.
Access control issues pose a significant challenge, and AI coding tools, in particular, have struggled to address this vulnerability class effectively, highlighting the need for developer skill and awareness. The impact of broken access control is significant. For example, if an attacker can access admin-only features, they could disable security settings, extract private information, or impersonate other users.
Secure coding practices counter these risks by enforcing server-side authorization checks for every request, following the principle of least privilege, and avoiding sole reliance on obscurity (such as hiding links) as a security measure. Additionally, conducting rigorous access control testing helps ensure that these protections remain strong over the long term.

Cross-site request forgery (CSRF)
Cross-site request forgery (CSRF) attacks force a user to perform an unwanted action on another site where they are authenticated. This might be transferring funds, changing an email address, or modifying account settings. The attack works because the browser automatically includes valid authentication tokens, like cookies, with the forged request.
Secure coding defends against CSRF by implementing anti-CSRF tokens that are unique to each user session and validating them with each state-changing request. Additional defenses include requiring re-authentication for critical actions and setting the SameSite attribute on cookies to prevent them from being sent with cross-site requests. By embedding these protections into the development lifecycle, you can make it much more likely that your system processes only legitimate, intentional actions.
Insecure authentication
Insecure authentication occurs when the process of verifying a user’s identity is weak, predictable, or otherwise flawed. This can result from poor password policies, insecure credential storage, or a lack of multi-factor authentication (MFA). Attackers can exploit these weaknesses through a variety of methods, including brute force attacks, credential stuffing, or intercepting unencrypted credentials in transit. The impact of insecure authentication is severe because it can give attackers direct access to user accounts, administrative controls, and sensitive data. Once inside, they can further compromise systems or make off with valuable information.
Secure coding addresses this vulnerability by enforcing strong password requirements, hashing and salting stored credentials, using secure protocols like HTTPS for all authentication exchanges, and integrating MFA to provide an additional layer of verification. Developers should also design login mechanisms to limit failed attempts and detect suspicious activity early, so authentication systems act as a strong line of defense rather than a weak point.
6 secure coding practices to follow
Building secure software involves more than knowing what threats exist. It requires learning and incorporating proven secure coding practices and patterns. The techniques below offer actionable steps developers can take to make security an integral part of every project.
1. Implement user access control
As noted above, user access control means defining and enforcing permissions for each user role in your system. Strong access control prevents unauthorized users from viewing sensitive data, modifying records, or performing administrative actions. It also limits the damage if a user account is compromised, since an attacker will only have the permissions of that account.
Effective user access control requires robust authentication to verify identity, followed by authorization checks to confirm that the authenticated user has permission to perform the requested action. You should regularly review your access control practices to align with the principle of least privilege, giving users the minimum access needed to do their jobs. Access control also relies on regular monitoring to keep policies and users in the system up to date, along with audits that quickly flag any unusual activity.
2. Validate and sanitize data
Validating and sanitizing data involves checking all incoming inputs to ensure they meet expected formats, types, and patterns before processing, then cleaning the data to remove potentially dangerous content. These practices should apply to incoming data from any external source, as even trusted sources can be compromised, so every input should be treated as untrusted until verified. By building validation and sanitization into the development process, you keep your application resilient against common threats like injection attacks.
3. Write in a modern language
Secure coding isn’t just about how you write code. It’s also about choosing tools and environments that make it easier to avoid introducing security flaws in the first place. While moving entirely to a modern language is often not a realistic or efficient option for many enterprises, making at least some use of a modern programming language — and using the latest version of all your chosen languages — can improve software security. Modern languages and frameworks typically offer better memory safety, stronger type checking, and built-in protection against common vulnerabilities. For example, languages like Rust and Go are designed with safety in mind, helping to prevent issues like buffer overflows that older languages may be more prone to.
Established languages like Java or Python can be difficult to modernize and secure, but keeping up with the most recent releases ensures you have access to the latest security features and performance improvements. Many updates patch known vulnerabilities, deprecate unsafe functions, and provide more secure default settings.
4. Practice code obfuscation
Code obfuscation is the process of making your source code or compiled code more difficult for attackers to understand, reverse-engineer, or manipulate. While it doesn’t replace other security measures, it adds another layer of defense by hiding the application’s logic and sensitive routines from prying eyes. Obfuscation can involve techniques like renaming variables and functions to meaningless identifiers or restructuring code in ways that make it harder to follow.
The goal is to raise the cost and effort required for an attacker to find and exploit vulnerabilities. In secure coding, obfuscation works alongside other strong security practices to make your application a less attractive target.

5. Scan and monitor your code
Secure coding practices also involve actively scanning and monitoring your code. Static application security testing (SAST) tools analyze your source code for known vulnerabilities before deployment, while dynamic application security testing (DAST) tools test running applications for exploitable flaws in real time. Combining both approaches helps you catch issues early and continuously.
Beyond scanning during development, it’s critical to implement ongoing monitoring in production. This involves setting up alerts for unusual activity, logging security events, and utilizing runtime application self-protection (RASP) tools to detect and block attacks in real-time. Regular scanning and monitoring ensure that even if vulnerabilities slip through during development, you have the visibility to address them rapidly before significant damage can be done.
6. Document and implement secure coding standards
Documenting secure coding standards consists of creating a clear set of guidelines that define how your team writes safe, maintainable, and compliant code. These standards should cover topics like input validation, error handling, encryption practices, and session management, as well as how to address common vulnerabilities specific to your tech stack.
Having these standards in place ensures that all developers, from junior engineers to senior architects, follow the same security principles. When paired with training and regular updates, these standards become a living resource that keeps your development process aligned with the latest security requirements.
Secure coding standards and frameworks
If you’re looking for help in crafting your own coding standards, the popular guidelines below can help. They cover a range of practices that address common vulnerabilities and can help clarify how to align your coding efforts with industry best practices.
OWASP Secure Coding Practices
OWASP is one of the most widely recognized sources for developers who want to embed security into their code from start to finish. It produces key secure coding resources like the OWASP Developer Guide and the OWASP Top 10. OWASP’s approach is highly actionable, offering checklists and coding tips that developers can apply during development.
Following OWASP guidelines benefits teams by creating a common baseline for secure coding across projects. Because OWASP is regularly updated to reflect new threat vectors and attack techniques, organizations can use it to stay ahead of emerging risks. By building OWASP’s principles into your workflow, you improve code quality, reduce vulnerabilities, and align with widely accepted industry guidelines.

NIST Secure Software Development Framework
The National Institute of Standards and Technology (NIST) publishes comprehensive secure coding guidance alongside broader cybersecurity frameworks. In addition to providing information on high-level secure software development practices, the NIST Secure Software Development Framework (SSDF) provides a common vocabulary that improves communication on key issues among and between teams at your company. It focuses on outcomes rather than specific techniques, so it's best as a complement to other standards like OWASP or the SEI CERT Coding Standards.
SEI CERT Coding Standards
Developed by the CERT Division at the Software Engineering Institute (SEI), the SEI CERT Coding Standards focus on preventing security vulnerabilities in specific programming languages, including C, C++, Java, and Perl. Each language-specific standard features secure coding rules, detailed explanations, and examples of both compliant and noncompliant code. As the CERT coding standards address the nuances and quirks of specific programming languages, they’re highly valuable and actionable for developers working in those environments.
Microsoft Security Development Lifecycle
Microsoft’s Security Development Lifecycle (SDL) is a set of practices designed to make security an integral part of the software development process. It includes recommendations on 10 important topics, including threat modeling, security training for developers, and securing the software supply chain. Microsoft uses this approach itself, so organizations benefit from a tested process that aligns developers, testers, and security teams.
ISO/IEC 27001
ISO/IEC 27001 is best known as a standard for information security management systems (ISMS), but it also has strong implications for secure coding. While it focuses on establishing an organization-wide ISMS, it includes principles on secure coding. These recommendations provide high level guidance organizations can follow when working to implement secure coding practices.

AI Security Rules
AI coding tools are more handy than ever, but they can do more harm than good if using them doesn’t result in safe, accurate code. Secure Code Warrior’s AI Security Rules — the first of their kind — provide guidance on secure coding best practices to use with AI tools like GitHub Copilot, Cline, Cursor, and Windsurf. These rules keep your AI coding assistants on track, putting guardrails in place that minimize the risk of insecure code.
Learn how to create secure code from the start
Secure coding is more than just a technical requirement — it’s a critical business advantage. When your team writes secure code from the start, you prevent costly vulnerabilities, reduce the risk of data breaches, and deliver software your customers can trust. Mastering secure coding practices, however, can be particularly challenging without structured guidance. Developers need real-world practice, up-to-date knowledge of evolving threats, and a way to apply security principles confidently in every line of code.
Secure Code Warrior’s ISO 27001 certified and SOC 2 compliant agile learning platform gives your team exactly that. With training on language-specific security best practices, realistic coding challenges, and content curated for a variety of roles, it turns security from an afterthought into a natural part of the development process. Developers build the skills to identify and fix vulnerabilities early, align with industry standards, and take full ownership of code security throughout the software development lifecycle. It's no surprise that companies that use Secure Code Warrior cut software vulnerabilities by 53%, realize cost savings of up to $14 million, and see 92% of their developers want additional training.
If you want to see how your team can write safer, stronger code from day one, book a Secure Code Warrior demo today.

When software vulnerabilities are treated as an afterthought or roadblock to innovation, organizations open the door to data breaches, reputational damage, and costly legal liabilities. Cyberattacks often exploit weaknesses in code that might have been prevented with stronger development practices.
Secure coding addresses these challenges by embedding security principles into every stage of development. Instead of implementing fixes after vulnerabilities are discovered, developers write code with built-in protections against common threats such as injection attacks and cross-site scripting (XSS). Let’s take a closer look at how secure coding can help your company reduce risk, safeguard user trust, and comply with regulatory requirements, all while delivering reliable, high-quality software.
What is secure coding?
Secure coding is the principle of following security best practices when writing software to address potential vulnerabilities. Rather than treating security as a separate phase of development, secure coding integrates proven safeguards from the earliest stages on, ensuring developers take ownership of code security and have the skills to apply it effectively.
Recognized secure coding standards produced by organizations like the Open Worldwide Application Security Project (OWASP), or the Software Engineering Institute’s CERT Division, can act as a North Star for developers looking to avoid common pitfalls that attackers exploit. Continuously building upon foundational, hands-on secure coding skills to safely implement these strategies into existing workflows is a non-negotiable in today's cybersecurity landscape. For example, validating as many user inputs as possible can prevent SQL injection attacks, while output encoding helps block XSS. These and other secure coding practices reduce the risk of breaches and lead to more resilient applications that can stand up to evolving cyber threats.
Why is secure coding so important?
Secure coding matters because many successful cyberattacks exploit vulnerabilities that could have been prevented during development. By prioritizing secure practices from the start, you reduce the likelihood of introducing flaws that attackers can use to compromise data or disrupt operations. Building security into every stage of the software development life cycle (SDLC) ensures that every feature, update, and integration is designed with protection in mind.
Proactively addressing risks during development is far less expensive than fixing them after deployment, where remediation can require emergency patches, downtime, and incident response resources. It improves compliance with data protection regulations as well, sidestepping potential fines and legal challenges. Secure coding practices also foster consumer trust in your company and make strong security part of your brand reputation.
Common code security vulnerabilities
Secure coding aims to prevent the most frequent and dangerous vulnerabilities that attackers exploit, in addition to emerging threat vectors, like those that come with the use of AI coding tools. Here is an overview of several common vulnerabilities, the damage they can cause, and how secure coding can help mitigate them.

Deserialization flaws
Deserialization flaws occur when an application accepts and processes data from external sources without proper validation. Serialization converts objects into a format that can be stored or transmitted, while deserialization reconstructs those objects for use. The impact of a deserialization flaw can be severe, resulting in the execution of arbitrary code or escalation of privileges. Secure coding addresses this by ensuring that only trusted, validated data is deserialized and by avoiding native deserialization of untrusted inputs entirely when possible.
Injection attacks
Injection attacks occur when an attacker supplies input that is interpreted as part of a command or query by the application. The most well-known type is an SQL injection, where malicious SQL statements are inserted into queries to access or alter database contents. Other types include command injections, where attackers execute arbitrary commands, and Lightweight Directory Access Protocol (LDAP) injections.The consequences of injection attacks are broad, ranging from unauthorized data access and deletion to full system compromise. Databases containing sensitive personal, financial, or proprietary information are prime targets. Secure coding helps prevent injection vulnerabilities by using parameterized queries or prepared statements, escaping untrusted data before it’s processed, and enforcing strict input validation. These and other secure coding practices can stop attackers from altering the intended behavior of the application.

Cross-site scripting (XSS)
Cross-site scripting (XSS) is a form of injection attack that targets web applications by inserting malicious scripts into pages viewed by other users. This typically happens when an application includes unvalidated user input in its output. When another user’s browser renders the page, the malicious script runs, potentially stealing cookies, capturing keystrokes, or redirecting them to malicious sites.
The impact of XSS can include session hijacking and identity theft. For businesses, this erodes customer trust and can lead to regulatory consequences if sensitive data is compromised. Secure coding addresses XSS by sanitizing and encoding all user-supplied input before it’s displayed, using frameworks that automatically escape output, and implementing a Content Security Policy (CSP) to limit what scripts can run.
Access control
Access control vulnerabilities occur when rules about what users can see or do are not properly defined or enforced. Broken access control lets attackers bypass intended user role restrictions, potentially reading sensitive data, modifying records, or performing actions intended only for privileged users.
Access control issues pose a significant challenge, and AI coding tools, in particular, have struggled to address this vulnerability class effectively, highlighting the need for developer skill and awareness. The impact of broken access control is significant. For example, if an attacker can access admin-only features, they could disable security settings, extract private information, or impersonate other users.
Secure coding practices counter these risks by enforcing server-side authorization checks for every request, following the principle of least privilege, and avoiding sole reliance on obscurity (such as hiding links) as a security measure. Additionally, conducting rigorous access control testing helps ensure that these protections remain strong over the long term.

Cross-site request forgery (CSRF)
Cross-site request forgery (CSRF) attacks force a user to perform an unwanted action on another site where they are authenticated. This might be transferring funds, changing an email address, or modifying account settings. The attack works because the browser automatically includes valid authentication tokens, like cookies, with the forged request.
Secure coding defends against CSRF by implementing anti-CSRF tokens that are unique to each user session and validating them with each state-changing request. Additional defenses include requiring re-authentication for critical actions and setting the SameSite attribute on cookies to prevent them from being sent with cross-site requests. By embedding these protections into the development lifecycle, you can make it much more likely that your system processes only legitimate, intentional actions.
Insecure authentication
Insecure authentication occurs when the process of verifying a user’s identity is weak, predictable, or otherwise flawed. This can result from poor password policies, insecure credential storage, or a lack of multi-factor authentication (MFA). Attackers can exploit these weaknesses through a variety of methods, including brute force attacks, credential stuffing, or intercepting unencrypted credentials in transit. The impact of insecure authentication is severe because it can give attackers direct access to user accounts, administrative controls, and sensitive data. Once inside, they can further compromise systems or make off with valuable information.
Secure coding addresses this vulnerability by enforcing strong password requirements, hashing and salting stored credentials, using secure protocols like HTTPS for all authentication exchanges, and integrating MFA to provide an additional layer of verification. Developers should also design login mechanisms to limit failed attempts and detect suspicious activity early, so authentication systems act as a strong line of defense rather than a weak point.
6 secure coding practices to follow
Building secure software involves more than knowing what threats exist. It requires learning and incorporating proven secure coding practices and patterns. The techniques below offer actionable steps developers can take to make security an integral part of every project.
1. Implement user access control
As noted above, user access control means defining and enforcing permissions for each user role in your system. Strong access control prevents unauthorized users from viewing sensitive data, modifying records, or performing administrative actions. It also limits the damage if a user account is compromised, since an attacker will only have the permissions of that account.
Effective user access control requires robust authentication to verify identity, followed by authorization checks to confirm that the authenticated user has permission to perform the requested action. You should regularly review your access control practices to align with the principle of least privilege, giving users the minimum access needed to do their jobs. Access control also relies on regular monitoring to keep policies and users in the system up to date, along with audits that quickly flag any unusual activity.
2. Validate and sanitize data
Validating and sanitizing data involves checking all incoming inputs to ensure they meet expected formats, types, and patterns before processing, then cleaning the data to remove potentially dangerous content. These practices should apply to incoming data from any external source, as even trusted sources can be compromised, so every input should be treated as untrusted until verified. By building validation and sanitization into the development process, you keep your application resilient against common threats like injection attacks.
3. Write in a modern language
Secure coding isn’t just about how you write code. It’s also about choosing tools and environments that make it easier to avoid introducing security flaws in the first place. While moving entirely to a modern language is often not a realistic or efficient option for many enterprises, making at least some use of a modern programming language — and using the latest version of all your chosen languages — can improve software security. Modern languages and frameworks typically offer better memory safety, stronger type checking, and built-in protection against common vulnerabilities. For example, languages like Rust and Go are designed with safety in mind, helping to prevent issues like buffer overflows that older languages may be more prone to.
Established languages like Java or Python can be difficult to modernize and secure, but keeping up with the most recent releases ensures you have access to the latest security features and performance improvements. Many updates patch known vulnerabilities, deprecate unsafe functions, and provide more secure default settings.
4. Practice code obfuscation
Code obfuscation is the process of making your source code or compiled code more difficult for attackers to understand, reverse-engineer, or manipulate. While it doesn’t replace other security measures, it adds another layer of defense by hiding the application’s logic and sensitive routines from prying eyes. Obfuscation can involve techniques like renaming variables and functions to meaningless identifiers or restructuring code in ways that make it harder to follow.
The goal is to raise the cost and effort required for an attacker to find and exploit vulnerabilities. In secure coding, obfuscation works alongside other strong security practices to make your application a less attractive target.

5. Scan and monitor your code
Secure coding practices also involve actively scanning and monitoring your code. Static application security testing (SAST) tools analyze your source code for known vulnerabilities before deployment, while dynamic application security testing (DAST) tools test running applications for exploitable flaws in real time. Combining both approaches helps you catch issues early and continuously.
Beyond scanning during development, it’s critical to implement ongoing monitoring in production. This involves setting up alerts for unusual activity, logging security events, and utilizing runtime application self-protection (RASP) tools to detect and block attacks in real-time. Regular scanning and monitoring ensure that even if vulnerabilities slip through during development, you have the visibility to address them rapidly before significant damage can be done.
6. Document and implement secure coding standards
Documenting secure coding standards consists of creating a clear set of guidelines that define how your team writes safe, maintainable, and compliant code. These standards should cover topics like input validation, error handling, encryption practices, and session management, as well as how to address common vulnerabilities specific to your tech stack.
Having these standards in place ensures that all developers, from junior engineers to senior architects, follow the same security principles. When paired with training and regular updates, these standards become a living resource that keeps your development process aligned with the latest security requirements.
Secure coding standards and frameworks
If you’re looking for help in crafting your own coding standards, the popular guidelines below can help. They cover a range of practices that address common vulnerabilities and can help clarify how to align your coding efforts with industry best practices.
OWASP Secure Coding Practices
OWASP is one of the most widely recognized sources for developers who want to embed security into their code from start to finish. It produces key secure coding resources like the OWASP Developer Guide and the OWASP Top 10. OWASP’s approach is highly actionable, offering checklists and coding tips that developers can apply during development.
Following OWASP guidelines benefits teams by creating a common baseline for secure coding across projects. Because OWASP is regularly updated to reflect new threat vectors and attack techniques, organizations can use it to stay ahead of emerging risks. By building OWASP’s principles into your workflow, you improve code quality, reduce vulnerabilities, and align with widely accepted industry guidelines.

NIST Secure Software Development Framework
The National Institute of Standards and Technology (NIST) publishes comprehensive secure coding guidance alongside broader cybersecurity frameworks. In addition to providing information on high-level secure software development practices, the NIST Secure Software Development Framework (SSDF) provides a common vocabulary that improves communication on key issues among and between teams at your company. It focuses on outcomes rather than specific techniques, so it's best as a complement to other standards like OWASP or the SEI CERT Coding Standards.
SEI CERT Coding Standards
Developed by the CERT Division at the Software Engineering Institute (SEI), the SEI CERT Coding Standards focus on preventing security vulnerabilities in specific programming languages, including C, C++, Java, and Perl. Each language-specific standard features secure coding rules, detailed explanations, and examples of both compliant and noncompliant code. As the CERT coding standards address the nuances and quirks of specific programming languages, they’re highly valuable and actionable for developers working in those environments.
Microsoft Security Development Lifecycle
Microsoft’s Security Development Lifecycle (SDL) is a set of practices designed to make security an integral part of the software development process. It includes recommendations on 10 important topics, including threat modeling, security training for developers, and securing the software supply chain. Microsoft uses this approach itself, so organizations benefit from a tested process that aligns developers, testers, and security teams.
ISO/IEC 27001
ISO/IEC 27001 is best known as a standard for information security management systems (ISMS), but it also has strong implications for secure coding. While it focuses on establishing an organization-wide ISMS, it includes principles on secure coding. These recommendations provide high level guidance organizations can follow when working to implement secure coding practices.

AI Security Rules
AI coding tools are more handy than ever, but they can do more harm than good if using them doesn’t result in safe, accurate code. Secure Code Warrior’s AI Security Rules — the first of their kind — provide guidance on secure coding best practices to use with AI tools like GitHub Copilot, Cline, Cursor, and Windsurf. These rules keep your AI coding assistants on track, putting guardrails in place that minimize the risk of insecure code.
Learn how to create secure code from the start
Secure coding is more than just a technical requirement — it’s a critical business advantage. When your team writes secure code from the start, you prevent costly vulnerabilities, reduce the risk of data breaches, and deliver software your customers can trust. Mastering secure coding practices, however, can be particularly challenging without structured guidance. Developers need real-world practice, up-to-date knowledge of evolving threats, and a way to apply security principles confidently in every line of code.
Secure Code Warrior’s ISO 27001 certified and SOC 2 compliant agile learning platform gives your team exactly that. With training on language-specific security best practices, realistic coding challenges, and content curated for a variety of roles, it turns security from an afterthought into a natural part of the development process. Developers build the skills to identify and fix vulnerabilities early, align with industry standards, and take full ownership of code security throughout the software development lifecycle. It's no surprise that companies that use Secure Code Warrior cut software vulnerabilities by 53%, realize cost savings of up to $14 million, and see 92% of their developers want additional training.
If you want to see how your team can write safer, stronger code from day one, book a Secure Code Warrior demo today.

Click on the link below and download the PDF of this resource.
Secure Code Warrior is here for your organization to help you secure code across the entire software development lifecycle and create a culture in which cybersecurity is top of mind. Whether you’re an AppSec Manager, Developer, CISO, or anyone involved in security, we can help your organization reduce risks associated with insecure code.
View reportBook a demoSecure Code Warrior makes secure coding a positive and engaging experience for developers as they increase their skills. We guide each coder along their own preferred learning pathway, so that security-skilled developers become the everyday superheroes of our connected world.
This article was written by Secure Code Warrior's team of industry experts, committed to empowering developers with the knowledge and skills to build secure software from the start. Drawing on deep expertise in secure coding practices, industry trends, and real-world insights.
When software vulnerabilities are treated as an afterthought or roadblock to innovation, organizations open the door to data breaches, reputational damage, and costly legal liabilities. Cyberattacks often exploit weaknesses in code that might have been prevented with stronger development practices.
Secure coding addresses these challenges by embedding security principles into every stage of development. Instead of implementing fixes after vulnerabilities are discovered, developers write code with built-in protections against common threats such as injection attacks and cross-site scripting (XSS). Let’s take a closer look at how secure coding can help your company reduce risk, safeguard user trust, and comply with regulatory requirements, all while delivering reliable, high-quality software.
What is secure coding?
Secure coding is the principle of following security best practices when writing software to address potential vulnerabilities. Rather than treating security as a separate phase of development, secure coding integrates proven safeguards from the earliest stages on, ensuring developers take ownership of code security and have the skills to apply it effectively.
Recognized secure coding standards produced by organizations like the Open Worldwide Application Security Project (OWASP), or the Software Engineering Institute’s CERT Division, can act as a North Star for developers looking to avoid common pitfalls that attackers exploit. Continuously building upon foundational, hands-on secure coding skills to safely implement these strategies into existing workflows is a non-negotiable in today's cybersecurity landscape. For example, validating as many user inputs as possible can prevent SQL injection attacks, while output encoding helps block XSS. These and other secure coding practices reduce the risk of breaches and lead to more resilient applications that can stand up to evolving cyber threats.
Why is secure coding so important?
Secure coding matters because many successful cyberattacks exploit vulnerabilities that could have been prevented during development. By prioritizing secure practices from the start, you reduce the likelihood of introducing flaws that attackers can use to compromise data or disrupt operations. Building security into every stage of the software development life cycle (SDLC) ensures that every feature, update, and integration is designed with protection in mind.
Proactively addressing risks during development is far less expensive than fixing them after deployment, where remediation can require emergency patches, downtime, and incident response resources. It improves compliance with data protection regulations as well, sidestepping potential fines and legal challenges. Secure coding practices also foster consumer trust in your company and make strong security part of your brand reputation.
Common code security vulnerabilities
Secure coding aims to prevent the most frequent and dangerous vulnerabilities that attackers exploit, in addition to emerging threat vectors, like those that come with the use of AI coding tools. Here is an overview of several common vulnerabilities, the damage they can cause, and how secure coding can help mitigate them.

Deserialization flaws
Deserialization flaws occur when an application accepts and processes data from external sources without proper validation. Serialization converts objects into a format that can be stored or transmitted, while deserialization reconstructs those objects for use. The impact of a deserialization flaw can be severe, resulting in the execution of arbitrary code or escalation of privileges. Secure coding addresses this by ensuring that only trusted, validated data is deserialized and by avoiding native deserialization of untrusted inputs entirely when possible.
Injection attacks
Injection attacks occur when an attacker supplies input that is interpreted as part of a command or query by the application. The most well-known type is an SQL injection, where malicious SQL statements are inserted into queries to access or alter database contents. Other types include command injections, where attackers execute arbitrary commands, and Lightweight Directory Access Protocol (LDAP) injections.The consequences of injection attacks are broad, ranging from unauthorized data access and deletion to full system compromise. Databases containing sensitive personal, financial, or proprietary information are prime targets. Secure coding helps prevent injection vulnerabilities by using parameterized queries or prepared statements, escaping untrusted data before it’s processed, and enforcing strict input validation. These and other secure coding practices can stop attackers from altering the intended behavior of the application.

Cross-site scripting (XSS)
Cross-site scripting (XSS) is a form of injection attack that targets web applications by inserting malicious scripts into pages viewed by other users. This typically happens when an application includes unvalidated user input in its output. When another user’s browser renders the page, the malicious script runs, potentially stealing cookies, capturing keystrokes, or redirecting them to malicious sites.
The impact of XSS can include session hijacking and identity theft. For businesses, this erodes customer trust and can lead to regulatory consequences if sensitive data is compromised. Secure coding addresses XSS by sanitizing and encoding all user-supplied input before it’s displayed, using frameworks that automatically escape output, and implementing a Content Security Policy (CSP) to limit what scripts can run.
Access control
Access control vulnerabilities occur when rules about what users can see or do are not properly defined or enforced. Broken access control lets attackers bypass intended user role restrictions, potentially reading sensitive data, modifying records, or performing actions intended only for privileged users.
Access control issues pose a significant challenge, and AI coding tools, in particular, have struggled to address this vulnerability class effectively, highlighting the need for developer skill and awareness. The impact of broken access control is significant. For example, if an attacker can access admin-only features, they could disable security settings, extract private information, or impersonate other users.
Secure coding practices counter these risks by enforcing server-side authorization checks for every request, following the principle of least privilege, and avoiding sole reliance on obscurity (such as hiding links) as a security measure. Additionally, conducting rigorous access control testing helps ensure that these protections remain strong over the long term.

Cross-site request forgery (CSRF)
Cross-site request forgery (CSRF) attacks force a user to perform an unwanted action on another site where they are authenticated. This might be transferring funds, changing an email address, or modifying account settings. The attack works because the browser automatically includes valid authentication tokens, like cookies, with the forged request.
Secure coding defends against CSRF by implementing anti-CSRF tokens that are unique to each user session and validating them with each state-changing request. Additional defenses include requiring re-authentication for critical actions and setting the SameSite attribute on cookies to prevent them from being sent with cross-site requests. By embedding these protections into the development lifecycle, you can make it much more likely that your system processes only legitimate, intentional actions.
Insecure authentication
Insecure authentication occurs when the process of verifying a user’s identity is weak, predictable, or otherwise flawed. This can result from poor password policies, insecure credential storage, or a lack of multi-factor authentication (MFA). Attackers can exploit these weaknesses through a variety of methods, including brute force attacks, credential stuffing, or intercepting unencrypted credentials in transit. The impact of insecure authentication is severe because it can give attackers direct access to user accounts, administrative controls, and sensitive data. Once inside, they can further compromise systems or make off with valuable information.
Secure coding addresses this vulnerability by enforcing strong password requirements, hashing and salting stored credentials, using secure protocols like HTTPS for all authentication exchanges, and integrating MFA to provide an additional layer of verification. Developers should also design login mechanisms to limit failed attempts and detect suspicious activity early, so authentication systems act as a strong line of defense rather than a weak point.
6 secure coding practices to follow
Building secure software involves more than knowing what threats exist. It requires learning and incorporating proven secure coding practices and patterns. The techniques below offer actionable steps developers can take to make security an integral part of every project.
1. Implement user access control
As noted above, user access control means defining and enforcing permissions for each user role in your system. Strong access control prevents unauthorized users from viewing sensitive data, modifying records, or performing administrative actions. It also limits the damage if a user account is compromised, since an attacker will only have the permissions of that account.
Effective user access control requires robust authentication to verify identity, followed by authorization checks to confirm that the authenticated user has permission to perform the requested action. You should regularly review your access control practices to align with the principle of least privilege, giving users the minimum access needed to do their jobs. Access control also relies on regular monitoring to keep policies and users in the system up to date, along with audits that quickly flag any unusual activity.
2. Validate and sanitize data
Validating and sanitizing data involves checking all incoming inputs to ensure they meet expected formats, types, and patterns before processing, then cleaning the data to remove potentially dangerous content. These practices should apply to incoming data from any external source, as even trusted sources can be compromised, so every input should be treated as untrusted until verified. By building validation and sanitization into the development process, you keep your application resilient against common threats like injection attacks.
3. Write in a modern language
Secure coding isn’t just about how you write code. It’s also about choosing tools and environments that make it easier to avoid introducing security flaws in the first place. While moving entirely to a modern language is often not a realistic or efficient option for many enterprises, making at least some use of a modern programming language — and using the latest version of all your chosen languages — can improve software security. Modern languages and frameworks typically offer better memory safety, stronger type checking, and built-in protection against common vulnerabilities. For example, languages like Rust and Go are designed with safety in mind, helping to prevent issues like buffer overflows that older languages may be more prone to.
Established languages like Java or Python can be difficult to modernize and secure, but keeping up with the most recent releases ensures you have access to the latest security features and performance improvements. Many updates patch known vulnerabilities, deprecate unsafe functions, and provide more secure default settings.
4. Practice code obfuscation
Code obfuscation is the process of making your source code or compiled code more difficult for attackers to understand, reverse-engineer, or manipulate. While it doesn’t replace other security measures, it adds another layer of defense by hiding the application’s logic and sensitive routines from prying eyes. Obfuscation can involve techniques like renaming variables and functions to meaningless identifiers or restructuring code in ways that make it harder to follow.
The goal is to raise the cost and effort required for an attacker to find and exploit vulnerabilities. In secure coding, obfuscation works alongside other strong security practices to make your application a less attractive target.

5. Scan and monitor your code
Secure coding practices also involve actively scanning and monitoring your code. Static application security testing (SAST) tools analyze your source code for known vulnerabilities before deployment, while dynamic application security testing (DAST) tools test running applications for exploitable flaws in real time. Combining both approaches helps you catch issues early and continuously.
Beyond scanning during development, it’s critical to implement ongoing monitoring in production. This involves setting up alerts for unusual activity, logging security events, and utilizing runtime application self-protection (RASP) tools to detect and block attacks in real-time. Regular scanning and monitoring ensure that even if vulnerabilities slip through during development, you have the visibility to address them rapidly before significant damage can be done.
6. Document and implement secure coding standards
Documenting secure coding standards consists of creating a clear set of guidelines that define how your team writes safe, maintainable, and compliant code. These standards should cover topics like input validation, error handling, encryption practices, and session management, as well as how to address common vulnerabilities specific to your tech stack.
Having these standards in place ensures that all developers, from junior engineers to senior architects, follow the same security principles. When paired with training and regular updates, these standards become a living resource that keeps your development process aligned with the latest security requirements.
Secure coding standards and frameworks
If you’re looking for help in crafting your own coding standards, the popular guidelines below can help. They cover a range of practices that address common vulnerabilities and can help clarify how to align your coding efforts with industry best practices.
OWASP Secure Coding Practices
OWASP is one of the most widely recognized sources for developers who want to embed security into their code from start to finish. It produces key secure coding resources like the OWASP Developer Guide and the OWASP Top 10. OWASP’s approach is highly actionable, offering checklists and coding tips that developers can apply during development.
Following OWASP guidelines benefits teams by creating a common baseline for secure coding across projects. Because OWASP is regularly updated to reflect new threat vectors and attack techniques, organizations can use it to stay ahead of emerging risks. By building OWASP’s principles into your workflow, you improve code quality, reduce vulnerabilities, and align with widely accepted industry guidelines.

NIST Secure Software Development Framework
The National Institute of Standards and Technology (NIST) publishes comprehensive secure coding guidance alongside broader cybersecurity frameworks. In addition to providing information on high-level secure software development practices, the NIST Secure Software Development Framework (SSDF) provides a common vocabulary that improves communication on key issues among and between teams at your company. It focuses on outcomes rather than specific techniques, so it's best as a complement to other standards like OWASP or the SEI CERT Coding Standards.
SEI CERT Coding Standards
Developed by the CERT Division at the Software Engineering Institute (SEI), the SEI CERT Coding Standards focus on preventing security vulnerabilities in specific programming languages, including C, C++, Java, and Perl. Each language-specific standard features secure coding rules, detailed explanations, and examples of both compliant and noncompliant code. As the CERT coding standards address the nuances and quirks of specific programming languages, they’re highly valuable and actionable for developers working in those environments.
Microsoft Security Development Lifecycle
Microsoft’s Security Development Lifecycle (SDL) is a set of practices designed to make security an integral part of the software development process. It includes recommendations on 10 important topics, including threat modeling, security training for developers, and securing the software supply chain. Microsoft uses this approach itself, so organizations benefit from a tested process that aligns developers, testers, and security teams.
ISO/IEC 27001
ISO/IEC 27001 is best known as a standard for information security management systems (ISMS), but it also has strong implications for secure coding. While it focuses on establishing an organization-wide ISMS, it includes principles on secure coding. These recommendations provide high level guidance organizations can follow when working to implement secure coding practices.

AI Security Rules
AI coding tools are more handy than ever, but they can do more harm than good if using them doesn’t result in safe, accurate code. Secure Code Warrior’s AI Security Rules — the first of their kind — provide guidance on secure coding best practices to use with AI tools like GitHub Copilot, Cline, Cursor, and Windsurf. These rules keep your AI coding assistants on track, putting guardrails in place that minimize the risk of insecure code.
Learn how to create secure code from the start
Secure coding is more than just a technical requirement — it’s a critical business advantage. When your team writes secure code from the start, you prevent costly vulnerabilities, reduce the risk of data breaches, and deliver software your customers can trust. Mastering secure coding practices, however, can be particularly challenging without structured guidance. Developers need real-world practice, up-to-date knowledge of evolving threats, and a way to apply security principles confidently in every line of code.
Secure Code Warrior’s ISO 27001 certified and SOC 2 compliant agile learning platform gives your team exactly that. With training on language-specific security best practices, realistic coding challenges, and content curated for a variety of roles, it turns security from an afterthought into a natural part of the development process. Developers build the skills to identify and fix vulnerabilities early, align with industry standards, and take full ownership of code security throughout the software development lifecycle. It's no surprise that companies that use Secure Code Warrior cut software vulnerabilities by 53%, realize cost savings of up to $14 million, and see 92% of their developers want additional training.
If you want to see how your team can write safer, stronger code from day one, book a Secure Code Warrior demo today.
Table of contents
Secure Code Warrior makes secure coding a positive and engaging experience for developers as they increase their skills. We guide each coder along their own preferred learning pathway, so that security-skilled developers become the everyday superheroes of our connected world.

Secure Code Warrior is here for your organization to help you secure code across the entire software development lifecycle and create a culture in which cybersecurity is top of mind. Whether you’re an AppSec Manager, Developer, CISO, or anyone involved in security, we can help your organization reduce risks associated with insecure code.
Book a demoDownloadResources to get you started
Cyber Resilience Act (CRA) Aligned Learning Pathways
SCW supports Cyber Resilience Act (CRA) readiness with CRA-aligned Quests and conceptual learning collections that help development teams build the Secure by Design, SDLC, and secure coding skills aligned with the CRA’s secure development principles.
Threat Modeling with AI: Turning Every Developer into a Threat Modeler
Walk away better equipped to help developers combine threat modeling ideas and techniques with the AI tools they're already using to strengthen security, improve collaboration, and build more resilient software from the start.
Resources to get you started
Cyber Resilience Act Explained: What It Means for Secure by Design Software Development
Learn what the EU Cyber Resilience Act (CRA) requires, who it applies to, and how engineering teams can prepare with secure by design practices, vulnerability prevention, and developer capability building.












%20(1).avif)
.avif)




