
Self-Paced Training
Rapidly enhance developer secure coding skills across the widest range of languages and frameworks. Our proven hyper-relevant learning platform embeds security into coding and mindset.

Embed secure code training into your team’s DNA
Rapidly enhance developer secure coding skills across the widest range of languages and frameworks. Our proven hyper-relevant learning platform embeds security into coding and mindset.

Secure coding training that inspires developers
Enhance your secure coding skills at your own pace with Secure Code Warrior's on-demand training. Accessible anytime and anywhere, this self-guided platform offers a wealth of resources tailored to developers' needs. As a crucial component of your organization's bespoke learning program, our training not only educates but also excites developers about the importance of cybersecurity. Dive deep into the latest security practices across various programming languages and frameworks, and become part of a proactive community prioritizing code safety. With Secure Code Warrior, transform the way you approach coding, ensuring security is integrated into every line of code you write.
- Applying secure architectures and design principles
- Equipping AI-assisted developers with adequate security knowledge
- Efficiently and effectively addressing code vulnerabilities


Security-First Development Culture, Made Easy
Secure Code Warrior empowers you to fundamentally change how your software is created by enabling you to set new standards for secure code. Our Developer Risk Management Platform helps you cultivate and maintain a security-first development culture, enabling you to measure, manage, and mitigate developer security risk through comprehensive benchmarking, robust governance, and engaging, hands-on education.
The Secure Code Warrior Difference
Data Driven Security Programs with SCW Trust Score
This industry-first benchmark helps quantify the impact of your secure coding initiatives. The SCW Trust Score® provides a comprehensive assessment of your organization’s secure coding skills, enabling AppSec teams and CISOs to gain a holistic understanding of their team's competencies and pinpoint areas for optimization and benchmark performance against peers.
Explore SCW Trust Score

Observability and Governance for Risk Management
SCW Trust Agent gives you visibility into the developers working with your code base, and insights into their security skills. You can then configure policies for code repositories to help improve your security posture through proactive governance at scale, ensuring that developers are appropriately trained in the language of their commits.
Explore SCW Trust AgentHands-On Training Activities & Industry-Leading Content
Get a dynamic, scalable and interactive education experience that empowers your developers with the secure coding skills they need, exactly when they need them. Our on-demand Agile Learning Platform goes far beyond basic compliance training. It contains over 600+ hours and growing of the latest and greatest secure code content spanning 600+ vulnerability topics (including AI/LLM security) across 70+ languages and frameworks.
Explore SCW Learning Platform

Broad Integration Ecosystem
We work where developers are. Secure Code Warrior fits seamlessly into your existing SDLC with integrations into a variety of different tools and services, from developer and appsec tools that offer just-in-time contextual training information and code management tools to educational tools where you can implement Secure Code Warrior within your own LMS and automation tools for easy onboarding.
Explore SCW IntegrationsExpert Guidance to Support Your Secure Code Journey
You don’t need to go at it alone. We’re here to help. Expert guidance and support are available at every level of program maturity. Whether you are just starting out, or looking to build a best-in-class program, Secure Code Warrior’s industry experts are there to guide you with Customer Support, Customer Success or optional Program Strategy Services to maximize the impact of your security initiatives.
Explore SCW Professional Services
Assessment Do’s & Don’ts
Assessment Dos
- Use real-world problems
- Include a variety of challenges
- Test for problem-solving abilities
- Evaluate soft skills
- Ensure fairness and objectivity
Assessment Don’ts
- Use unrealistic time constraints
- Solely rely on Whiteboard Coding
- Forget about code readability
- Neglect security
Practical knowledge and training
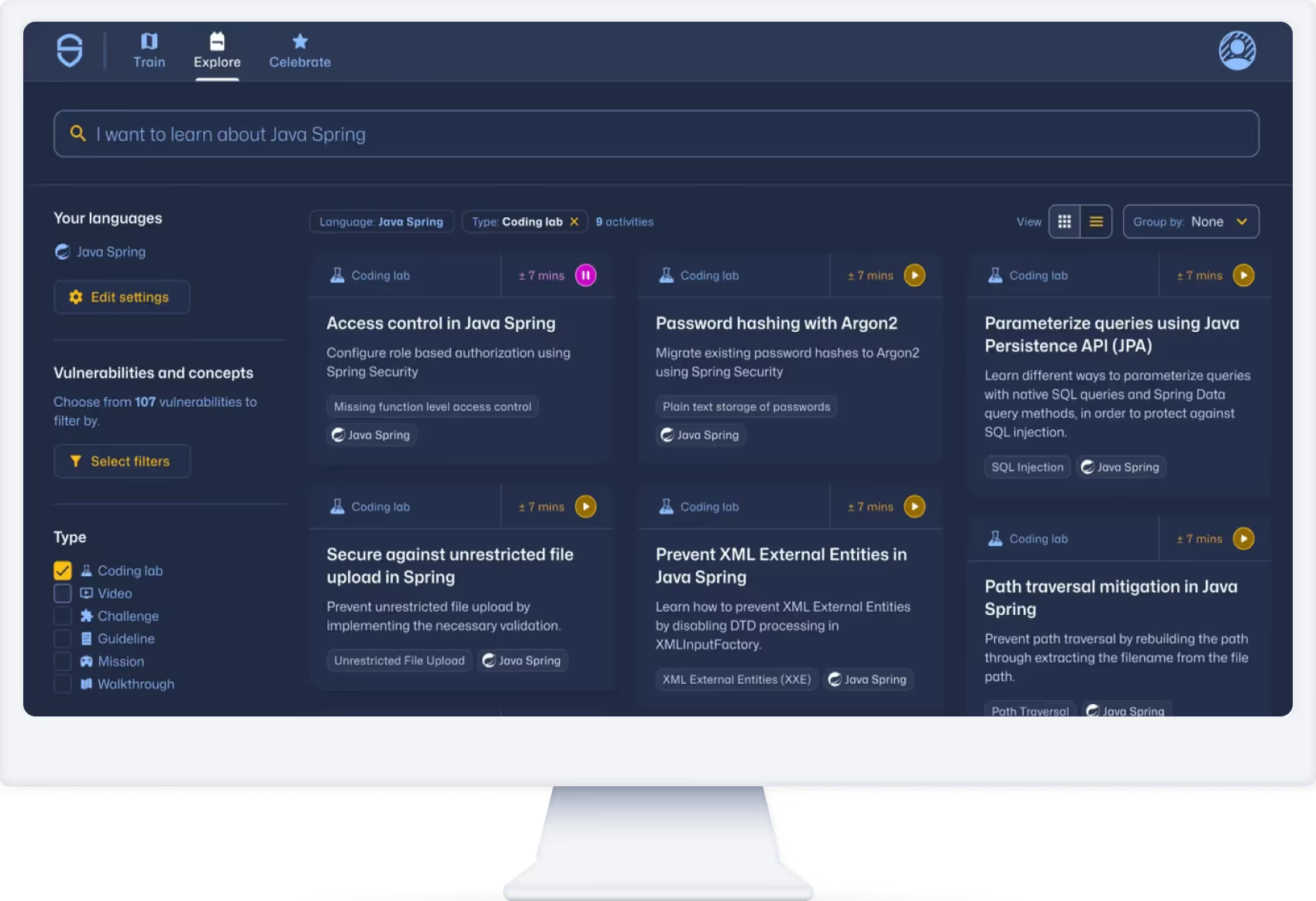
Our content library is like an ever-expanding universe of code, packed with goodies for every coder out there. Imagine having over 60 programming frameworks and more than 8,000 challenges at your fingertips, covering every security hiccup you can think of – that’s over 150 types of security vulnerabilities! It’s not just big; it’s designed to keep you ahead of the curve, constantly updated with the latest in coding and security. Whether you’re battling common bugs like SQL injections or tackling the trickier stuff, we’ve got your back. Dive in, play around, and boost your coding skills in the most fun way possible. Welcome to your new playground!



Practical knowledge and training for security superheroes.
Select your preferred language
Select from over 60 programming languages and frameworks to train in a way that's relevant.
This personalized approach ensures you're not just learning; you're enhancing your skills in the technologies you use daily. It's all about making your learning experience as applicable and impactful as possible, directly benefiting your projects and career by keeping your skills sharp and up-to-date in the ever-evolving tech landscape. Whether you’re coding in Python, wrestling with React, or navigating Node.js, training tailored to your needs means you’re always on top of your game.


Explore the Training Ground
Focus on finding and fixing specific types of application security weaknesses with in-depth training in a sandbox environment to hone your skills.
By zeroing in on identifying and remedying specific types of application security weaknesses, our in-depth training offers a hands-on sandbox environment where you can really sharpen your skills. This focused approach allows you to tackle the nuances of different vulnerabilities directly, learning by doing. It’s an invaluable opportunity to experiment, make mistakes, and learn in a safe, controlled setting, away from the pressures of real-world consequences.
Discover the Mission Control
Complete a set of quests in the most critical and most common application weaknesses.
These quests are designed to equip you with the knowledge and skills needed to tackle the vulnerabilities that developers frequently encounter. This hands-on experience is invaluable, as it mirrors real-world challenges, ensuring that what you learn is not only relevant but immediately applicable. Successfully navigating through these quests means you'll be better prepared to safeguard your applications against prevalent security threats, making you a more proficient and security-conscious developer.

Secure coding in action

Fundamentals redefined

Featured article
Cut vulnerabilities by 53%
- Reduce risk of breach
- Minimize vulnerabilities
- Secure your data
Things to Know about Developer Risk Management
What is Developer Risk Management?
Developer Risk Management is a holistic and proactive approach to application security, focused on code contributors rather than within the bits and bytes of the application layer itself.
The philosophy behind Developer Risk Management is that, through upskilling code contributors in a programmatic way, it exponentially increases the benefits and impact of secure code initiatives, leading to faster but more secure releases and significantly lowering potential cybersecurity risk.
Are you able to help me address my compliance requirements?
Yes!
Secure Code Warrior’s Developer Risk Management Platform provides the necessary relevant training materials needed, like content around the OWASP Top 10, to meet annual security training requirements for developers focused on secure coding techniques and a security-aware development workforce for compliance regulations like PCI DSS, ISO 27001, SOC 2, GDPR, and HIPAA.
Is Developer Risk Management similar to Secure by Design?
The concept of Developer Risk Management is closely related to guidelines surrounding Secure by Design and other Shift Left-type regulations being implemented worldwide.
While policy continues to evolve around setting guidelines and standards for software security, in practice, we have seen that this could be interpreted in a number of different ways.
Developer Risk Management is a practical approach to improving security posture whether related to initiatives around a Secure-by-Design pledge, some other governing force, or just a desire to enhance customer confidence to gain a competitive edge.
What kind of impact does managing developer risk have on my organization?
Many Secure Code Warrior customers have seen a significant impact across their organization when adopting a more proactive approach to managing developer risk. Including reducing vulnerabilities by up to 53%, accelerating development through improving MTTR by 3x, improving harmony between security and engineering teams, providing growth opportunities to developers, helping retain them, and fostering greater customer confidence and loyalty.
Resources to get you started
Benchmarking Security Skills: Streamlining Secure-by-Design in the Enterprise
The Secure-by-Design movement is the future of secure software development. Learn about the key elements companies need to keep in mind when they think about a Secure-by-Design initiative.
10 Key Predictions: Secure Code Warrior on AI & Secure-by-Design’s Influence in 2025
Organizations are facing tough decisions on AI usage to support long-term productivity, sustainability, and security ROI. It’s become clear to us over the last few years that AI will never fully replace the role of the developer. From AI + developer partnerships to the increasing pressures (and confusion) around Secure-by-Design expectations, let’s take a closer look at what we can expect over the next year.
Reactive Versus Preventive Security: Prevention Is a Better Cure
The idea of bringing preventive security to legacy code and systems at the same time as newer applications can seem daunting, but a Secure-by-Design approach, enforced by upskilling developers, can apply security best practices to those systems. It’s the best chance many organizations have of improving their security postures.
Driving Meaningful Success for Enterprise Secure-by-Design Initiatives
Our latest research paper, Benchmarking Security Skills: Streamlining Secure-by-Design in the Enterprise is the result of deep analysis of real Secure-by-Design initiatives at the enterprise level, and deriving best practice approaches based on data-driven findings.






.avif)

